Defensive Publishing of Proof of Existence
Easily Verify and Safeguard Your Creative Works and Discoveries!
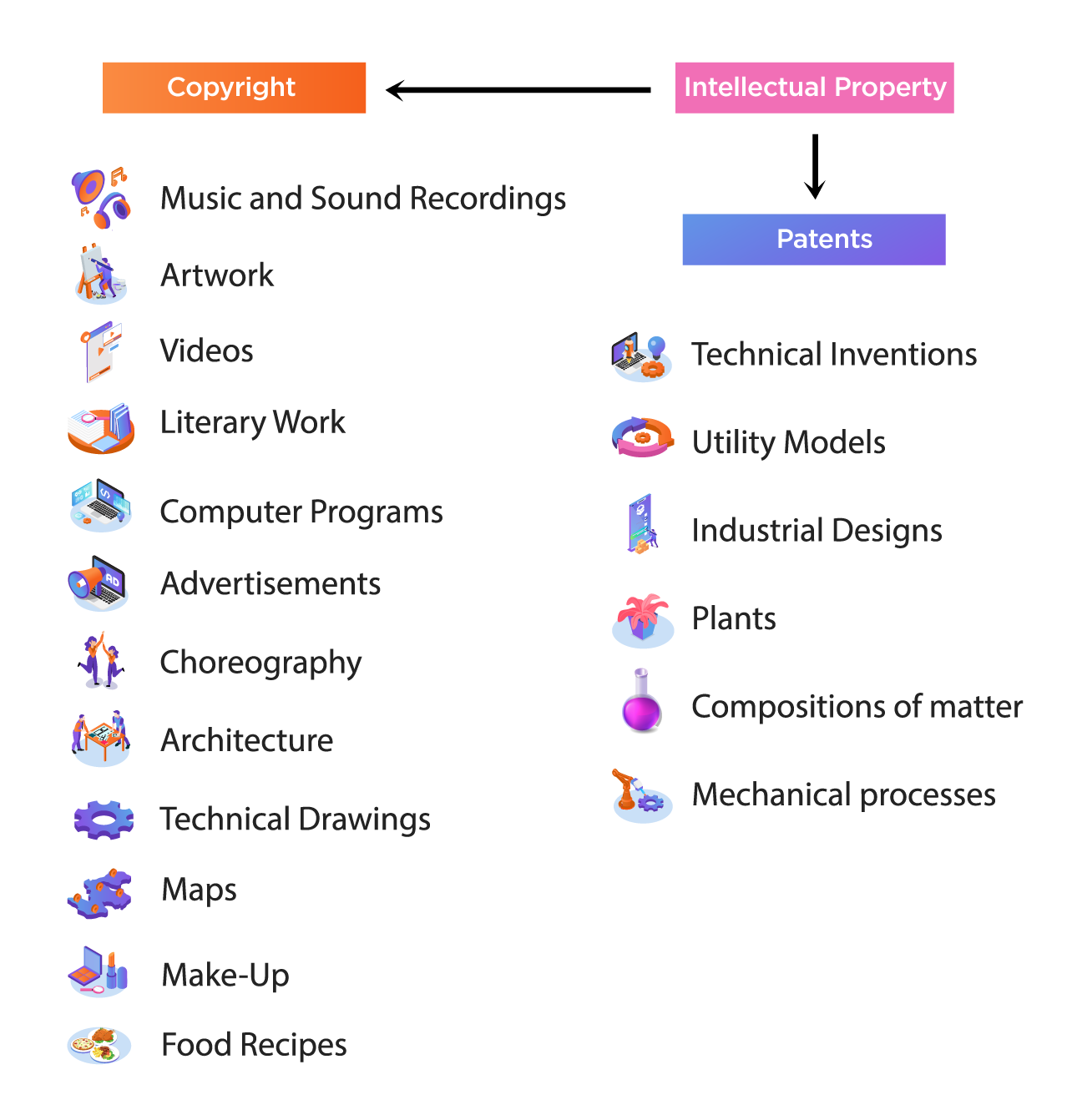
Protecting intellectual property can be a daunting task, typically involving patenting or publishing.
Patenting secures your copyright but demands a lengthy, intricate process with numerous requirements, such as utility models, industrial design patents, and mechanical processes. Additionally, patenting is eventually necessary but can be too expensive in the early phases of your scientific or engineering work.
Publishing, on the other hand, grants copyright to your literary, musical, or graphical creations but exposes them to the public domain. While this allows others to view and reference your work, it may not suit those desiring to keep their creations confidential but still have proof of authorship available.
In both cases, originality and applicability are crucial factors, making the verification and protection of your intellectual property a top priority.
We provide an affordable solution for verifying authorship, via Proof of Existence without requiring the publication of your creative work.
Secure your IP or other information
How the process works
How does it work?
The Solution works on 4 principles
-
Defensive Publishing of
For the purposes of protecting your work, defensive publishing provides electronic or non-constructive evidence that the information exists in a digital file format at certain time and date – powered by blockchain as an immutable record of your work.
Music and Sound Artwork Video Literature Computer Programs Utility ModelsIndustrial DesignsMechanical ProcessesProof for InsuranceIn this context, while the file itself will not be submitted, the data or contents of this cannot be changed at later stage.

Non-Constructive Evidence
With this, you can digitally validate the existence of your work, but this has a limitation in that you can’t use this PoE to re-create the original information in any way.
The evidence will be the only piece of information stored. All you need to do is to make sure that the file to be protected will remain intact and unedited.

as Proof of Existence (PoE)
Think of this as a code. This ‘code’ is in fact a cryptographic key created in SHA-256 – a cryptographic hash algorithm assigned to a file to corroborate its existence.
Each hash number is completely unique, and no two are ever the same. This is extremely useful as it can then verify work as your own.

stored in Public Blockchain
A public blockchain is one where anyone is free to join and participate in the core activities of the blockchain network. Anyone can read, write, and audit the ongoing activities on a public blockchain network, which helps achieve the self-governed, decentralized nature often touted when blockchain is discussed.
In this instance, The Proof Of makes use of a decentralized blockchain as an immutable record of your work. Once approved, this record can’t ever be deleted or changed. With thousands of independent validators that approve transactions, even if the chain is somehow hacked or compromised, it is impossible to alter any already-existing data.

Generate hash value
Protect Your intellectual property Now

